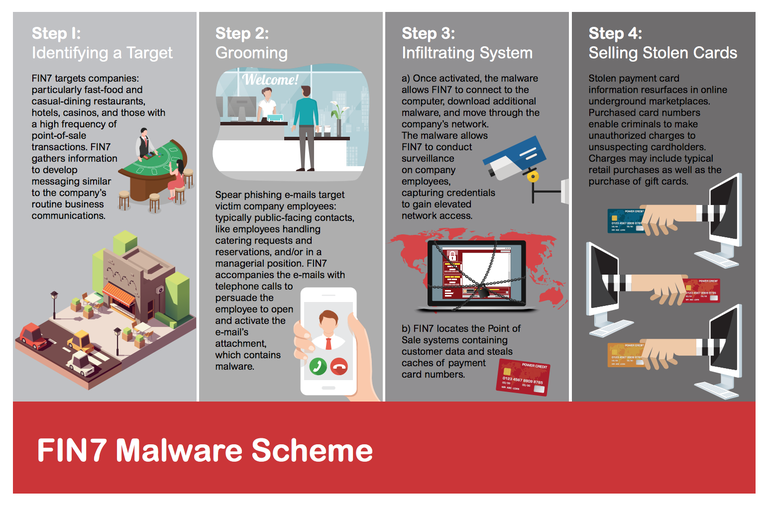
Project Lakhta is the name of a Russian project that was further documented by the Department of Justice last Friday in the form of sharing a Criminal Complaint against Elena Alekseevna Khusyaynova, said to be the accountant in charge of running a massive organization designed to inject distrust and division into the American elections and American society in general.
![]() |
| https://www.justice.gov/opa/press-release/file/1102316/download |
In a fairly unusual step, the 39 page Criminal Complaint against Khusyaynova, filed just last month in Alexandria, Virginia, has already been unsealed, prior to any indictment or specific criminal charges being brought against her before a grand jury. US Attorney G. Zachary Terwilliger says "The strategic goal of this alleged conspiracy, which continues to this day, is to sow discord in the U.S. political system and to undermine faith in our democratic institutions."
The data shared below, intended to summarize the 39 page criminal complaint, contains many direct quotes from the document, which has been shared by the DOJ. ( Click for
full Criminal Complaint against Elena Khusyaynova )
Since May 2014 the complaint shows that the following organizations were used as cover to spread distrust towards candidates for political office and the political system in general.
Internet Research Agency LLC ("IRA")
Internet Research LLC
MediaSintez LLC
GlavSet LLC
MixInfo LLC
Azimut LLC
NovInfo LLC
Nevskiy News LLC ("NevNov")
Economy Today LLC
National News LLC
Federal News Agency LLC ("FAN")
International News Agency LLC ("MAN")
These entities employed hundreds of individuals in support of Project Lakhta's operations with an annual global budget of millions of US dollars. Only some of their activity was directed at the United States.
Prigozhin and Concord
Concord Management and Consulting LLC and Concord Catering (collectively referred to as "Concord") are related Russian entities with various Russian government contracts. Concord was the primary source of funding for Project Lakhta, controlling funding, recommending personnel, and overseeing activities through reporting and interaction with the management of various Project Lakhta entities.
Yevgeniy Viktorovich Prigozhin is a Russian oligarch closely identified with Russian President Vladimir Putin. He began his career in the food and restaurant business and is sometimes referred to as "Putin's Chef." Concord has Russian government contracts to feed school children and the military.
Prigozhin was previously indicted, along with twelve others and three Russian companies, with committing federal crimes while seeking to interfere with the US elections and political process, including the 2016 presidential election.
Project Lakhta internally referred to their work as "information warfare against the United States of America" which was conducted through fictitious US personas on social media platforms and other Internet-based media.
Lakhta has a management group which organized the project into departments, including a design and graphics department, an analysts department, a search-engine optimization ("SEO") department, an IT department and a finance department.
Khusyaynova has been the chief accountant of Project Lakhta's finance department since April of 2014, which included the budgets of most or all of the previously named organizations. She submitted hundreds of financial vouchers, budgets, and payments requests for the Project Lakhta entities. The money was managed through at least 14 bank accounts belonging to more Project Lakhta affiliates, including:
Glavnaya Liniya LLC
Merkuriy LLC
Obshchepit LLC
Potentsial LLC
RSP LLC
ASP LLC
MTTs LLC
Kompleksservis LLC
SPb Kulinariya LLC
Almira LLC
Pishchevik LLC
Galant LLC
Rayteks LLC
Standart LLC
Project Lakhta Spending
Monthly reports were provided by Khusyaynova to Concord about the spendings for at least the period from January 2016 through July 2018.
A document sent in January 2017 including the projected budget for February 2017 (60 million rubles, or roughly $1 million USD), and an accounting of spending for all of calendar 2016 (720 million rubles, or $12 million USD). Expenses included:
Registration of domain names
Purchasing proxy servers
Social media marketing expenses, including:
- purchasing posts for social networks
- advertisements on Facebook
- advertisements on VKontakte
- advertisements on Instagram
- promoting posts on social networks
Other expenses were for Activists, Bloggers, and people who "developed accounts" on Twitter to promote online videos.
In January 2018, the "annual report" for 2017 showed 733 million Russian rubles of expenditure ($12.2M USD).
More recent expenses, between January 2018 and June 2018, included more than $60,000 in Facebook ads, and $6,000 in Instagram ads, as well as $18,000 for Bloggers and Twitter account developers.
Project Lakhta Messaging
From December 2016 through May 2018, Lakhta analysts and activist spread messages "to inflame passions on a wide variety of topics" including:
- immigration
- gun control and the Second Amendment
- the Confederate flag
- race relations
- LGBT issues
- the Women's March
- and the NFL national anthem debate.
Events in the United States were seized upon "to anchor their themes" including the Charleston church shootings, the Las Vegas concert shootings, the Charlottesville "Unite the Right" rally, police shootings of African-American men, and the personnel and policy decisions of the Trump administration.
Many of the graphics that were shared will be immediately recognizable to most social media users.
![]() |
| "Rachell Edison" Facebook profile |
The graphic above was shared by a confirmed member of the conspiracy on December 5, 2016. "Rachell Edison" was a Facebook profile controlled by someone on payroll from Project Lakhta. Their comment read "Whatever happens, blacks are innocent. Whatever happens, it's all guns and cops. Whatever happens, it's all racists and homophobes. Mainstream Media..."
The Rachell Edison account was created in September 2016 and controlled the Facebook page "Defend the 2nd". Between December 2016 and May 2017, "while concealing its true identity, location, and purpose" this account was used to share over 700 inflammatory posts related to gun control and the Second Amendment.
Other accounts specialized on other themes. Another account, using the name "Bertha Malone", was created in June 2015, using fake information to claim that the account holder lived in New York City and attended a university in NYC. In January 2016, the account created a Facebook page called "Stop All Invaders" (StopAI) which shared over 400 hateful anti-immigration and anti-Islam memes, implying that all immigrants were either terrorists or criminals. Posts shared by this acount reached 1.3 million individuals and at least 130,851 people directly engaged with the content (for example, by liking, sharing, or commenting on materials that originated from this account.)
Some examples of the hateful posts shared by "Bertha Malone" that were included in the DOJ criminal complaint, included these:
The latter image was accompanied by the comment:
"Instead this stupid witch hunt on Trump, media should investigate this traitor and his plane to Islamize our country. If you are true enemy of America, take a good look at Barack Hussein Obama and Muslim government officials appointed by him."
Directions to Project Lakhta Team Members
The directions shared to the propaganda spreaders gave very specific examples of how to influence American thought with guidance on what sources and techniques should be used to influence particular portions of our society. For example, to further drive wedges in the Republican party, Republicans who spoke out against Trump were attacked in social media:
(all of these are marked in the Criminal Complaint as "preliminary translations of Russian text"):
"Brand McCain as an old geezer who has lost it and who long ago belonged in a home for the elderly. Emphasize that John McCain's pathological hatred towards Donald Trump and towards all his initiatives crosses all reasonable borders and limits. State that dishonorable scoundrels, such as McCain, immediately aim to destroy all the conservative voters' hopes as soon as Trump tries to fulfill his election promises and tries to protect the American interests."
"Brand Paul Ryan a complete and absolute nobody incapable of any decisiveness. Emphasize that while serving as Speaker, this two-faced loudmouth has not accomplished anything good for America or for American citizens. State that the only way to get rid of Ryan from Congress, provided he wins in the 2018 primaries, is to vote in favor of Randy Brice, an American veteran and an iron worker and a Democrat."
Frequently the guidance was in relation to a particular news headline, where directions on how to use the headline to spread their message of division where shared. A couple examples of these:
After a news story "Trump: No Welfare To Migrants for Grants for First 5 Years" was shared, the conspiracy was directed to twist the messaging like this:
"Fully support Donald Trump and express the hope that this time around Congress will be forced to act as the president says it should. Emphasize that if Congress continues to act like the Colonial British government did before the War of Independence, this will call for another revolution. Summarize that Trump once again proved that he stands for protecting the interests of the United States of America."
In response to an article about scandals in the Robert Mueller investigation, the direction was to use this messaging:
"Special prosecutor Mueller is a puppet of the establishment. List scandals that took place when Mueller headed the FBI. Direct attention to the listed examples. State the following: It is a fact that the Special Prosector who leads the investigation against Trump represents the establishment: a politician with proven connections to the U.S. Democratic Party who says things that should either remove him from his position or disband the entire investigation commission. Summarize with a statement that Mueller is a very dependent and highly politicized figure; therefore, there will be no honest and open results from his investigation. Emphasize that the work of this commission is damaging to the country and is aimed to declare impeachement of Trump. Emphasize that it cannot be allowed, no matter what."
Many more examples are given, some targeted at particular concepts, such as this direction regarding "Sanctuary Cities":
"Characterize the position of the Californian sanctuary cities along with the position of the entire California administration as absolutely and completely treacherous and disgusting. Stress that protecting an illegal rapist who raped an American child is the peak of wickedness and hypocrisy. Summarize in a statement that "sanctuary city" politicians should surrender their American citizenship, for they behave as true enemies of the United States of America"
Some more basic guidance shared by Project Lakhta was about how to target conservatives vs. liberals, such as "if you write posts in a liberal group, you must not use Breitbart titles. On the contrary, if you write posts in a conservative group, do not use Washington Post or BuzzFeed's titles."
We see the "headline theft" implied by this in some of their memes. For example, this Breitbart headline:
Became this Project Lakhta meme (shared by Stop All Immigrants):
Similarly this meme originally shared as a quote from the Heritage Foundation, was adopted and rebranded by Lakhta-funded "Stop All Immigrants":
Twitter Messaging and Specific Political Races
Many Twitter accounts shown to be controlled by paid members of the conspiracy were making very specific posts in support of or in opposition to particular candidates for Congress or Senate. Some examples listed in the Criminal Complaint include:
@CovfefeNationUS posting:
Tell us who you want to defeat! Donate $1.00 to defeat @daveloebsack Donate $2.00 to defeat @SenatorBaldwin Donate $3.00 to defeat @clairecmc Donate $4.00 to defeat @NancyPelosi Donate $5.00 to defeat @RepMaxineWaters Donate $6.00 to defeat @SenWarren
Several of the Project Lakhta Twitter accounts got involved in the Alabama Senate race, but to point out that the objective of Lakhta is CREATE DISSENT AND DISTRUST, they actually tweeted on opposite sides of the campaign:
One Project Lakhta Twitter account, @KaniJJackson, posted on December 12, 2017:
"Dear Alabama, You have a choice today. Doug Jones put the KKK in prison for murdering 4 young black girls. Roy Moore wants to sleep with your teenage daughters. This isn't hard. #AlabamaSenate"
while on the same day @JohnCopper16, also a confirmed Project Lakhta Twitter account, tweeted:
"People living in Alabama have different values than people living in NYC. They will vote for someone who represents them, for someone who they can trust. Not you. Dear Alabama, vote for Roy Moore."
@KaniJJackson was a very active voice for Lakhta. Here are some additional tweets for that account:
"If Trump fires Robert Mueller, we have to take to the streets in protest. Our democracy is at stake." (December 16, 2017)
"Who ended DACA? Who put off funding CHIP for 4 months? Who rejected a deal to restore DACA? It's not #SchumerShutdown. It's #GOPShutdown." (January 19, 2018)
@JohnCopper16 also tweeted on that topic:
"Anyone who believes that President Trump is responsible for #shutdown2018 is either an outright liar or horribly ignorant. #SchumerShutdown for illegals. #DemocratShutdown #DemocratLosers #DemocratsDefundMilitary #AlternativeFacts" (January 20, 2018)
@KaniJJackson on Parkland, Florida and the 2018 Midterm election:
"Reminder: the same GOP that is offering thoughts and prayers today are the same ones that voted to allow loosening gun laws for the mentally ill last February. If you're outraged today, VOTE THEM OUT IN 2018. #guncontrol #Parkland"
They even tweet about themselves, as shown in this pair of tweets!
@JemiSHaaaZzz (February 16, 2018):
"Dear @realDonaldTrump: The DOJ indicted 13 Russian nationals at the Internet Research Agency for violating federal criminal law to help your campaign and hurt other campaigns. Still think this Russia thing is a hoax and a witch hunt? Because a lot of witches just got indicted."
@JohnCopper16 (February 16, 2018):
"Russians indicted today: 13 Illegal immigrants crossing Mexican border indicted today: 0 Anyway, I hope all those Internet Research Agency f*ckers will be sent to gitmo."
The Russians are also involved in "getting out the vote" - especially of those who hold strongly divisive views:
@JohnCopper16 (February 27, 2018):
"Dem2018 platform - We want women raped by the jihadists - We want children killed - We want higher gas prices - We want more illegal aliens - We want more Mexican drugs And they are wondering why @realDonaldTrump became the President"
@KaniJJackson (February 19, 2018):
"Midterms are 261 days, use this time to: - Promote your candidate on social media - Volunteer for a campaign - Donate to a campaign - Register to vote - Help others register to vote - Spread the word We have only 261 days to guarantee survival of democracy. Get to work!
More recent tweets have been on a wide variety of topics, with other accounts expressing strong views around racial tensions, and then speaking to the Midterm elections:
@wokeluisa (another confirmed Project Lakhta account):
"Just a reminder that: - Majority black Flint, Michigan still has drinking water that will give you brain damage if consumed - Republicans are still trying to keep black people from voting - A terrorist has been targeting black families for assassination in Austin, Texas"
and then, also @wokeluisa: (March 19, 2018):
"Make sure to pre-register to vote if you are 16 y.o. or older. Don't just sit back, do something about everything that's going on because November 6, 2018 is the date that 33 senate seats, 436 seats in the House of Representatives and 36 governorships will be up for re-election."
And from @johncopper16 (March 22, 2018):
"Just a friendly reminder to get involved in the 2018 Midterms. They are motivated They hate you They hate your morals They hate your 1A and 2A rights They hate the Police They hate the Military They hate YOUR President"
Some of the many additional Twitter accounts controlled by the conspiracy mentioned in the Criminal Complaint:
@UsaUsafortrump, @USAForDTrump, @TrumpWithUSA, @TrumpMov, @POTUSADJT, @imdeplorable201, @swampdrainer659, @maga2017trump, @TXCowboysRawk, @covfefeNationUS, @wokeluisa (2,000 tweets and at least 55,000 followers), @JohnCopper16, @Amconvoice, @TheTrainGuy13, @KaniJJackson, @JemiSHaaaZzz