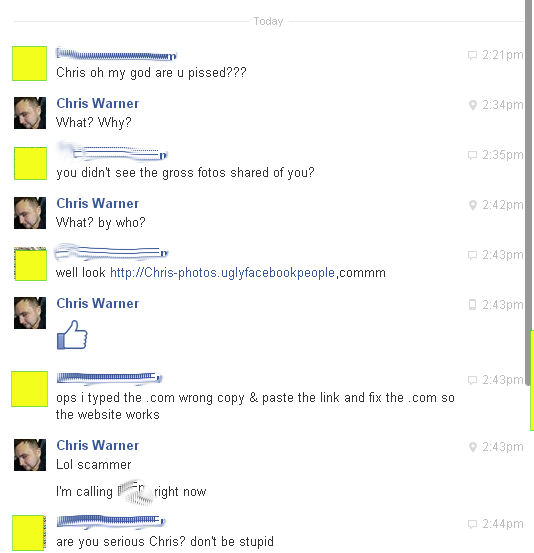
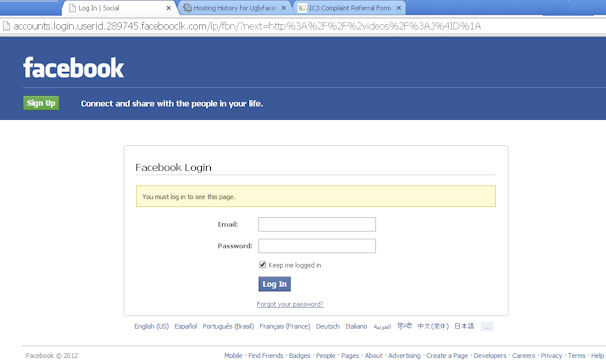
Today the U.S. government unsealed its indictment against Fifty-Five members of the Carder.su carding forum. We wrote about Carder.su before on this blog, back in March 2009 when a rival gang was trying to call attention to Carder.su by sending out spam advertising the site. (See:
Carders do battle through spam - carder.su. No wonder they were jealous! Today's indictment shows the Carder.su guys performed over $50 Million in fraudulent charges!
Named in the indictment were 39 individuals, all charged with "General Allegations" called:
Count One (Participate in a Racketeer Influenced Corrupt Organization [RICO])
and
Count Two (Conspiracy to Engage in a Racketeer Influenced Corrupt Organization).
The whole group are described in the indictment like this:
"The defendants herein, and others known and unknown, are members of, employed by, and associates of a criminal organization, hereafter referred to as "the Carder.su organization," whose members engage in acts of identity theft and financial fraud, including, but not limited to, acts involving trafficking in stolen means of identification; trafficking in, production and use of couterfeit identification documents; identity theft; trafficking in, production and use of unauthorized and counterfeit access devices; and bank fraud; and whose members interfere with interstate and foreign commerce through acts of identity theft and financial fraud. Members and associates of the Carder.su organization operate principally in Las Vegas, Nevada, and elsewhere.
Here's the list:
| NAME | AKA List | Counts Charged |
| Roman Zolotarev | Admin, Support | 1-2, 19 |
| Konstantin Lopatin | Graf | 1-2, 33, 44, 47 |
| Alexander Kostyukov * | Temp, KLBS | 1-2, 3-17 |
| Maceo Boozer III | XXXSimone, G4, El Padrino, Mr. Right, MRDC87 | 1-2, 3-17 |
| Tin-Yueng Wong | Ray Wong, Ray | 1-2, 3-17 |
| Edward Montecalvo * | N1ghtmare, Tenure44 | 1-2, 3-17, 22-55 |
| Yu Feng Wang | Ibatistuta | 1-2 |
| Mohamed Amr Mahmoud | Amr Mahmoud, CC--Trader, Kengza | 1-2, 20, 22-55 |
| Jermaine Smith | SirCharlie57, FairBusinessman | 1-2, 61-62 |
| Makyl Haggerty | Wave | 1-2 |
| Aladelola Teslim Ajayi | Bank Manager, Document Manager, Corey | 1-2, 61-62 |
| Alexandru Ion | AbagnaleFrank | 1-2 |
| Jordan Georgievski | Devica | 1-2 |
| Roman Seleznev | Track2, Bulba, NCUX | 1-2, 22-55 |
| Qasir Mukhtar | Caliber | 1-2, 56-60 |
| Roy Ayad | Rabie Ayad, Patistota | 1-2, 22-55 |
| Mina Morris | Source | 1-2, 22-55 |
| Rachid Idaali | C4rd3r | 1-2, 22-55 |
| Liridon Musliu | Bowl | 1-2, 22-55 |
| Sergei Litvinenko | Dorbik, Matad0r | 2 |
| Michael Lofton | Killit, Lofeazy | 1-2, 3-17 |
| Shiyang Gou | CDER | 1-2, 3-17 |
| David Ray Camez | Badman, DoctorSex | 1-2, 3-17 |
| Cameron Harrison | Kilobit | 1-2, 3-17 |
| Aleksandar Besarovic | Qiller | 1-2, 3-17 |
| Duvaughn Butler | Mackmann | 1-2, 21, 61-62 |
| Fredrick Thomas | 1Stunna | 1-2 |
| John Doe 1 | Senna071 | 1-2, 3-17 |
| John Doe 2 | Morfiy | 1-2, 3-17 |
| John Doe 3 | Gruber | 1-2, 18 |
| John Doe 4 | Maxxtro | 1-2 |
| John Doe 5 | Elit3 | 1-2 |
| John Doe 6 | Fozzy | 1-2, 22-55 |
| John Doe 7 | Vitrum, Lermentov | 1-2, 22-55 |
| Andrei Bolovan | Panther, Euphoric, Darkmth | 1-2, 22-55 |
| John Doe 8 | TM | 1-2, 22-55 |
| John Doe 9 | Zo0mer, Deputat | 1-2, 22-55 |
| John Doe 10 | Centurion | 1-2, 22-55 |
| John Doe 11 | Consigliori | 1-2, 61-62 |
While it is true that many carders are Russian, several folks on this list reside in the United States. This case, which DHS ICE calls "Operation: Open Market", has already seen 19 arrested in the United States, primarily in Las Vegas, where LOFTON, CAMEZ, BUTLER, LAMB, and VERGNETTI were arrested. (Some of those arrested are indicted separately and do not appear above.
KOSTYUKOV was arrested in Miami from his home at 1100 Washington Avenue, Miami Beach. (He sent a letter to the judge asking for his property back, including his Hookah pipe and his Dr. Dre Beats headphones.
KOSTYUKOV, 27, was arrested in Miami, Florida.
Boozer, 23, was arrested in Detroit, Michigan.
Montecalvo, 20, was arrested in Morgantown, WV.
Jermaine Smith, 31, was arrested in Newark, NJ
Makyl Haggerty, 22, lived in San Francisco,
Qasir Mukhtar, 27, in New York
Shiyang Gou, 27, in New York
Cameron Harrison, 25, in Augusta, GA
Fredrick Thomas, 31, in Orlando, FL
Omar Butt, 28, in New York
Bill Steffey, 33, in Sacramento,
Jason Maclaskey, 32, (at large?)
Derek Carder, 38, Sacramento
Robert Kephart, 38, Sacramento
Heather Dale, 21, Springfield, Orlando
Herbert Morrell, 50, Orlando
Roger Grodesky, 49, Warren, Ohio
John Holsheimer, 53, San Diego
David Ray Camez, a Nevada resident, for example, was convicted and was due to be sentenced today. (You may enjoy reading his Forfeiture document which includes ATM machines, PVC Card Embossers, dozens of phones and computers as well as printers, cameras, and video games. Camez was already serving a seven year sentence in the State of Arizona for fraud charges he was convicted of there.
Back in 2012, ICE agents announced that they had arrested 19 in the US in an operation called "Operation: Open Market."
The full
Fifty-one page indictment, originally introduced in court on January 10, 2012, and finally unsealed April 10, 2014, goes on to describe additional charges and activities, sometimes in great detail. The case against "Defendant 24, Cameron Harrison, AKA Kilobit" is being tried in Las Vegas, Nevada as CASE #: 2:12-cr-00004-APG-GWF-24.
The event that triggered the unsealing of the indictment was that Cameron Harrison pleaded guilty, WITHOUT BENEFIT OF A PLEA AGREEMENT! His nineteen page guilty plea. In addition to Count One and Count Two above, Cameron plead guilty to:
Count Sixteen: Trafficking in and Production of False Identification Documents and Aiding and Abetting, in violation of 18 U.S.C. § 1028(a)(1), (b)(1)(A)(ii), and (c)(3) and 18 U.S.C. § 2.
The Sentencing Guidelines that the prosecution is asking for are HUGE because they are describing the "Total amount of actual loss involved in the offense as $50,893,166.35" which gives a +24 to the Sentencing guidelines just for the financial losses!
Base Offense Level = 7
+ 24 (offense involved more than $50 Million of actual loss)
+6 (offense involved more than 250 victims)
+2 (offense involved receiving stolen property and the defendant was a person in the business of receiving and selling stolen property)
+2 (fraud committed from outside the US, involving a sophisticated means)
+2 (fraud involving possession of device-making equipment and trafficking in unauthorized and counterfeit access devices)
-3 (Acceptance of Responsibility)
Total Offense Level = 40
Restitutions that are declared in the Plea include:
American Express = $3,299,210.90
Discover Financial Services = $2,202,429.00
Master Card = $15,496,221.00
Visa Inc. = $29,895,305.45
Total = $50,895,305.45
Because this is a RICO case, EACH member of the Conspiracy can be found responsible for the full restitution. The Indictment requests that each have $20 million of their assets seized to help cover the costs. (Most have nowhere near that amount, of course...).
Roles of the Defendants
Despite the news headlines being about Kilobit (Cameron Harrison) today, Harrison was only a "Member" of the board. Far more important members are listed below by their roles on the various Carder.su websites.
Administrator = "Roman ZOLOTAREV was the head of Carder.su.
As the head of the governing council, the administrator handles day to day management decisions of the organizatoin, as well as long-term strategic planning for its continued viability. Zolotarev was the leader of the enterprise, appointing moderators, and directing other members and associates of the enterprise in carrying out unlawful and other activities in futherance of the conduct of the enterprise's affiars. In addition, ZOLOTAREV:
- determines which individuals can become and remain members of the Carder.su organization.
- regulates the functions, responsibilities, and levels of access to information accorded to each member.
- bestows the rewards accorded members for their loyalty to the Carder.su organization, and sets the punishments to be meted out to members evidencing disloyalty to the organization.
- decides when, how, and under what circumstances to attack and to retaliate against members of rival criminal organizations and their associated Internet website forums.
- has full access to, and privileges on, the computer servers hosting the Carder.su organization's websites.
- has ultimate responsibility for the administration, maintenance, anonymity and security of ther Carder.su organization's computer servers
Moderators = Konstantin LOPATIN and MAXXTRO
These defendants act as leaders of the enterprise, directing other members and associates in carrying out unlawful and other activities in furtherance of the conduct of the enterprise's affairs. Moderators are members of the Carder.su organization's governing counsel. They oversee and manage one or more subject matter specific areas on the Carder.su organization's websites. Their jobs included assisting Zolotarev by:
- monitoring and policing websites by editing and deleting members' posts and mediating disputes among members.
- serve as Reviewers for products or services through the enterprise with which they have expertise.
- Both LOPATIN and MAXXTRO possessed at least 15 counterfeit or unauthorized access devices.
Reviewers Members are allowed to sell contraband, including counterfeit documents, stolen bank accounts, and credit card information. Reviewers examine and test products and services that members wish to advertise and sell on the websites. A favorable review is a prerequisite to to selling contraband. Any member can be appointed to do a review, although they are usually done by Moderators or the Administrator.
Vendors
Vendors advertise and sell products, services, and other contraband after receiving a favorable review.
Vendors among the defendants included:
Alexander KOSTYUKOV (Temp/Klbs) - a vendor of Cashout services. Cashout vendors remove funds from bank and credit card accounts and receive a fee between 45% and 62% of the funds received.
Maceo BOOZER (XXXSimone / G4 / El Padrino / Mr. Right / mrdc87) is a vendor of dumps. "Dumps" are stolen credit and debit card account data. They sold for between $15 and $150 per card, depending on the quantity purchased and the geographic location. United States cards are least expensive, and European cards are most expensive.
Ray WONG is a vendor of counterfeit plastic. A device-making implement used to produce counterfeit credit cards. WONG sold blank counterfeit plastic cards for $20 to $25 each, with a minimum order of 50 cards. Embossed counterfeit cards were $65 to $75 each with a minimum order of ten. Wong was also a vendor of dumps.
MONTECALVO (N1ghtmare / Tenure44) is a vendor or dumps, but also offered a dump checking service. He had the ability to validate a card against a real financial institution.
Yu Feng WANG (Ibatistuta) is a vendor of counterfeit cards, counterfeit holograms, and signature panels used to manufacture counterfeit credit cards. He sold blanks for $10-$15 each.
Mohamed Amr Mahmoud (AMR Mahmoud / CC--Trader / Kengza) is a vendor of CVV. While dumps are magnetic card stripe reads, CVVs are all of the account holder information - such as Name, DOB, SSN, address, telephone number, mother's maiden name, and the CVV2 code from the back of the card. MAHMOUD also sold Paypal accounts, Fullz (all of the above plus expiration date and PIN), and Enroll/COBs. The latter included all of the previous data, as well as username and password for the account's online access. Depending on the online balance, he would charge $140 to $200 per account.
Jermaine SMITH (Sircharlie57 / Fairbusinessman) is a vendor of plastic and counterfeit cards.
Makyl HAGGERTY (Wave) is a vendor of counterfeit identification documents and counterfeit cards. He sold counterfeit drivers license for between $100 and $200 each, depending on state, including CA, TX, WI, OH, RI, NV, PA, IL, FL, LA, AZ, HA, SC, GA, NJ, as well as BC Canada. He also sold blank counterfeit plastics and embossed cards.
Aladelola Teslim AJAYI is a vendor of counterfeit identification documents, stolen corporate account information, dumps, and counterfeit credit cards.
ALEXANDRUION (Abagnalefrank) is a vendor of dumps. He sells 100 mixed Visa and Master Card accounts for $1,500 or 100 AmEx cards for $1,000.
Jordan GEORGIEVSKI is a vendor of counterfeit credit cards and blank plastic, as well as embossed cards for $75 each.
Roman SELEZNEV (Track2 / Bulba / Neux ) is a vendor of dumps. He sold very large volume product through an automated website where members could load their desired cards into a shopping cart. Accounts sold for $20 each.
Qasir MUKHTAR (Caliber) is a vendor of counterfeit plastics, holograms, and signature panels.
Roy AYAD (Rabie Ayad / Patistota) is a vendor of CVVs, selling through an automated website.
Mina MORRIS (Source) is a vendor of dumps. Morris had an automated website to sell dumps.
Rachid IDAALI (C4rd3r) is a vendor of Fullz.
Liridon MUSLIU (Bowl) is a vendor of CVVs.
Sergei Litvinenko (Dorbik / Matad0r ) is a vendor of Bullet Proof Hosting services and infrastructure for criminal websites. These are ISPs that allow criminals to run illegal websites used for phishing, carding forums, or dump sites.
GRUBER is a vendor of counterfeit identification documents including drivers licenses ranging from $150 to $200 each.
ELIT3 is a vendor of Fullz. He also sells Enroll/COBs.
FOZZY is a vendor of dumps ranging from $12 to $100 each, depending on quantity and location.
VITRUM (Lermentov) is a vendor of dumps.
Andrei BOLOVAN (Panther / Euphoric / Darkmth) is a vendor of dumps.
TM is a vendor of dumps and CVVs, which he sells to members through an automated website.
Zo0mer (Deputat) is a vendor of stolen PayPal accounts, Proxies, Fullz, Credit Card Checking and Information Lookups.
CENTURION is a vendor of dumps.
CONSIGLIORI is a vendor of dumps and blank plastic.
Members
Members must successfully complete a number of security features intended to keep out law enforcement and rival criminal organizations. Teams use a number of Carder.su websites as "virtual clubhouses" to gather with other members in order to share information, solicit and recruit other members and to achieve the common objectives of the enterprise.
Members charged in this conspiracy include:
Michael LOFTON (Killit / Lofeazy
Shiyang GOU (Cder)
David Ray CAMEZ (Bad Man / DoctorSex )
Cameron HARRISON (Kilobit)
Alexsandar BESAROVIC (Qiller)
Duvaughn BUTLER (Mackmann)
Fredrick THOMAS (1STunna )
SENNa071
MORFIY
The Charges
Count One and Two given above deal with Racketeering:
COUNT ONE:
Acts 1 through 15 - Unlawful Trafficking In and Production of False Identification Documents
Acts 16, 17, 19 - Attempt to Unlawfully Produce False Identification Documents
Acts 18, 20, 21 - Conspiracy to Unlawfully Produce False Identification Documents
Act 22 - Conspiracy to Unlawfully Transfer False Identification Documents
Act 23 - Possession of Document-Making Implements
Act 24 - Conspiracy to Unlawfully Transfer, Possess, and Use a Means of Identification
RACKETEERING ACTS 25 through 36
Acts of Wirefraud by MAXXTRO, MAHMOUD, HARRISON, ELIT3, LOFTON, THOMAS, MAHMOUD, ION, AYAD
RACKETEERING ACTS INVOLVING COUNTERFEIT AND UNAUTHORIZED ACCESS DEVICES
Act 37 - Using and Trafficking in Unauthorized Access Devices
Acts 38 through 97 - Possession of 15 or more Unauthorized Access Devices
Acts 98 through 103 - Trafficking In and Possessing Access Device-Making Equipment
Acts 104 through 109 - Conspiracy to Trafficking In and Possess Access Device-Making Equipment
COUNT TWO
Dealing with General Allegations from November 22, 2005 through June 2011. Counts Three Through Seventeen - Trafficking in and Production of False Identification Documents
Count Eighteen - Attempting to Unlawfully Produce False Identification Documents, Aiding and Abetting
Count Nineteen - Conspiracy to Unlawfully Transfer False Identification Documents
Count Twenty - Unlawful Transfer, Possession and Use of a Means of Identification, Aiding and Abetting
Count Twenty-One - Trafficking in and Use of Counterfeit and Unauthorized Access Devices, Aiding and Abetting
Counts Twenty-Two through Fifty-Five - Possession of Fifteen or More Counterfeit and Unauthorized Access Devices, Aiding and Abetting
Counts Fifty-Six through Sixty - Trafficking In and Possessing Access Device-Making Equipment; Aiding and Abetting
Counts Sixty-One and Sixty-Two - Conspiracy to Traffick In and Possess Access Device-Making Equipment